Unauthorized remote access to your iPhone poses a serious security threat. To check if someone is accessing your iPhone remotely, sign in to your Apple ID. Then, go to the “Devices” section and carefully examine the list of unfamiliar devices or third-party apps you don’t recognize or own.
In this guide, we’ll teach you how to tell if someone is accessing your iPhone remotely and how to solve it.
This Article Covers:
Can Someone Access My iPhone From Another Device?
Given how advanced technology is nowadays, you can expect there to be some underhanded means to gain access to an electronic device. Such unsolicited access can happen to your iPhone either through hacking, malicious software, or spyware.
In the case of iPhones, the most common way for attackers to access your device, its contents, or social media accounts is through hacking your Apple account. The implications may include:
- Disclosing all your passwords and login credentials
- Harming your financial accounts
- Serious security threats to your private information
- Unauthorized control and monitoring of your iPhone
The scary thing about iPhone remote access is that it is barely noticeable. Unless you’re really keen on the subtle details happening on your device and iCloud account, it would be hard for the untrained eye to recognize the symptoms of remote access.
Typical Indicators of Remote Access to Your iPhone
The only way to detect possible remote access on your device is by familiarizing yourself with its typical indicators. Although these indicators don’t necessarily mean that your Apple ID iPhone is being accessed remotely, they should be enough reason for you to conduct a check. Here are some things you should check out:
1. Faster Data Usage
If you’re not doing anything data-intensive on your iPhone, signs of faster data usage may indicate remote access by means of spyware. These pieces of software run in the background, continuously retrieving and sending your data to a website or a server.
Spyware often doesn’t filter what it sends, so it takes a lot of data to transmit everything. Consider investigating the cause if you’re consuming your data plan more quickly than usual.
2. Bizarre Battery Usage
If, for some reason, you notice your iOS phone’s battery life is draining more quickly, it can be a sign that some unauthorized apps are running in the background. Even if these apps aren’t actively controlling your device, such as the usage of the camera or microphone, they still run constantly.
This means your phone doesn’t really enter sleep mode, even if the screen is turned off. In turn, your phone battery’s life shortens. Meanwhile, faster battery usage shouldn’t cause worry if you’re actively doing power-hungry processes on your iPhone (e.g., playing games and long hours of video streaming).
3. Warm Battery When in Sleep Mode
It’s worth noting that it is pretty normal for your phone to heat up when you use it, especially when gaming or after using it for a long time. However, it shouldn’t be the case when you turn the screen off or put it in sleep mode.
If your phone gets hot while in sleep mode, something might be using its CPU. This is a typical scenario for spyware.
4. Slow iPhone Performance
With extensive data usage, unusual CPU activity, and unauthorized apps running in the background, your iPhone’s performance will likely slow down. You might notice this when your iOS apps appear laggy or when it takes longer for them to load. Worse, your iPhone may even crash.
5. Unusual Notifications
Receiving unusual emails and notifications can be a sign of a security threat. One example is a push notification that appears even when you have closed your web browser. This usually involves adware having penetrated your device.
6. Unauthorized Password Changes
A password change is one of the most common things you will notice when someone accesses your iPhone remotely. You can either receive an email notification about this change or be automatically locked out of your accounts.
If you can’t log back in using your known phone password, it could be a confirmation that someone is remotely controlling it without authorization.
How To Tell If Someone Is Accessing Your iPhone Remotely
Aside from the unusual signs mentioned above, you can also actively check for signs of remote access in the following aspects:
1. Check for Unrecognized Signed-in Devices
You actually have the option to see which devices your Apple ID account is signed into. If you see any unknown applications or unrecognizable accounts, you should immediately remove any account access besides those you use. These unrecognized devices might be remotely controlling your iPhone from somewhere else.
Here’s how to see your signed-in devices:
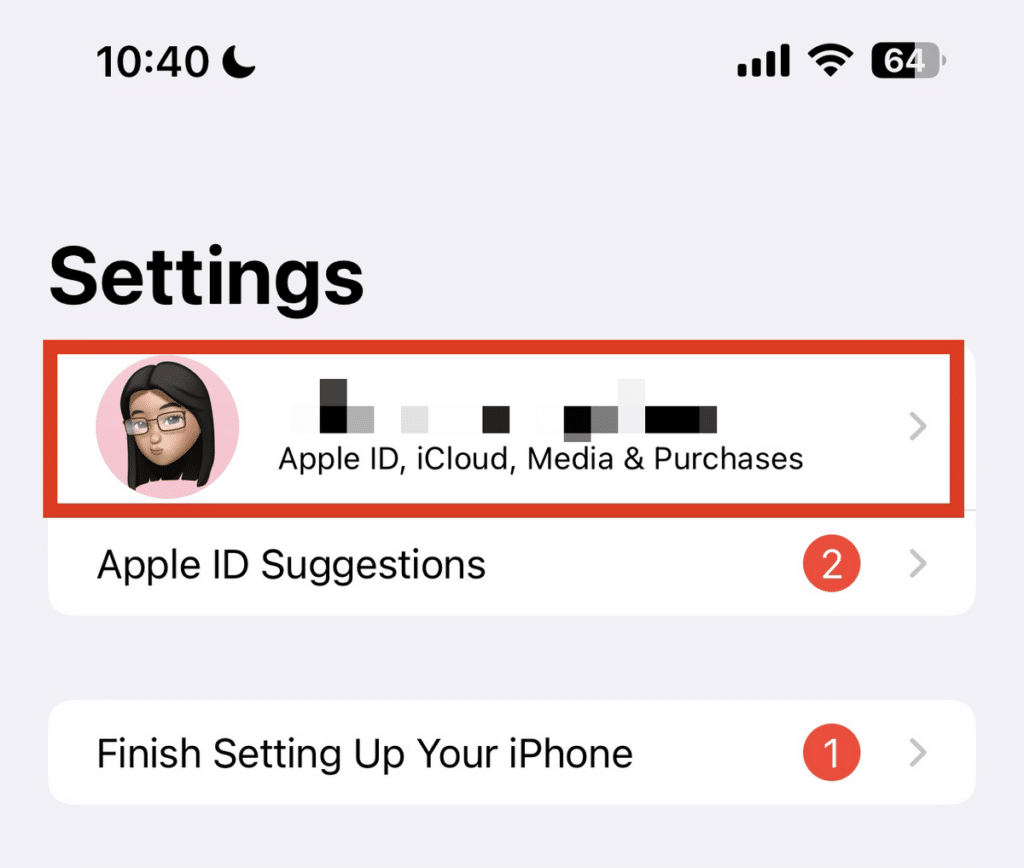
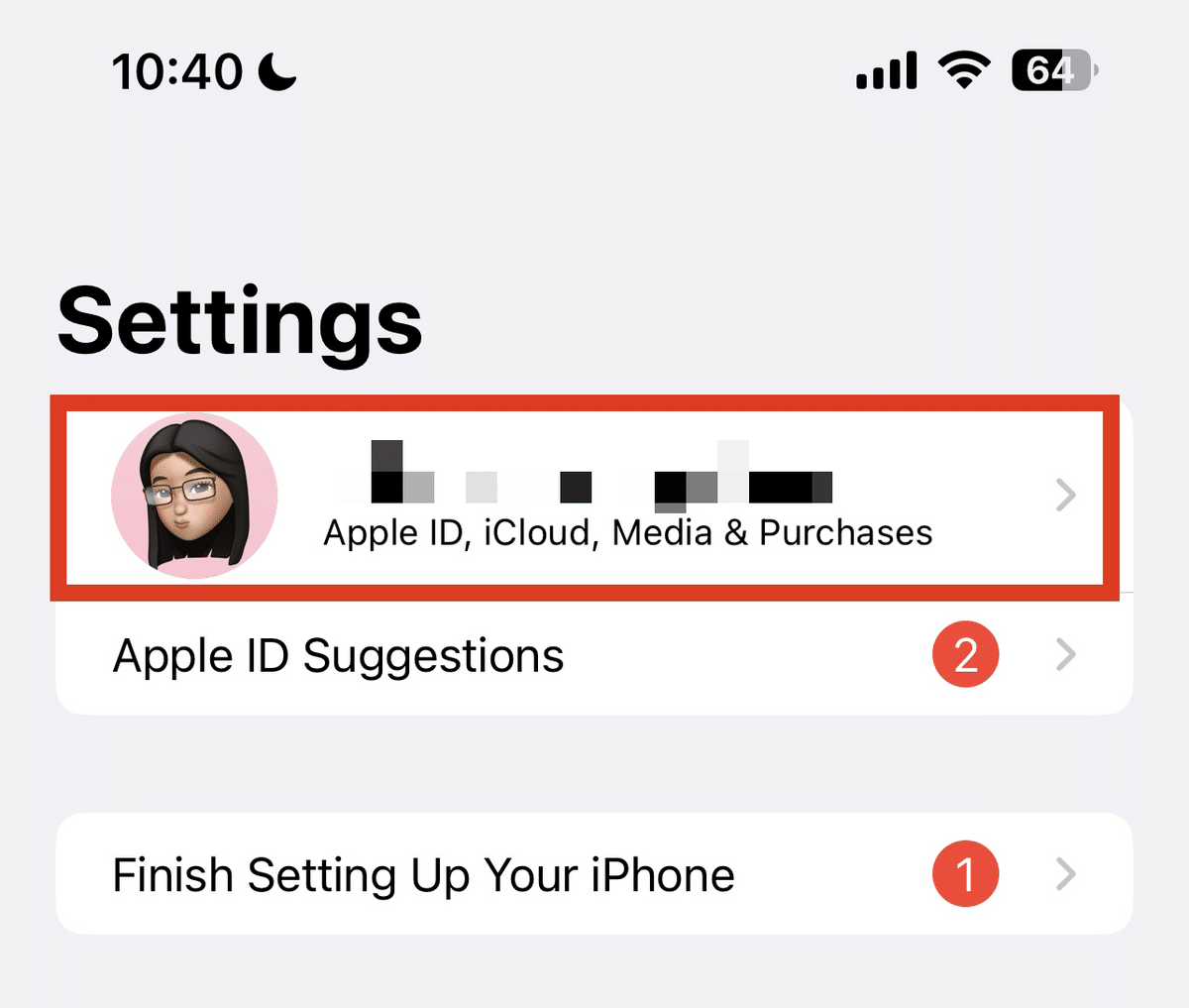
- Open the “Settings” menu on your iPhone.
- Tap your name and scroll down.
- See the list of devices where your Apple ID is logged in.
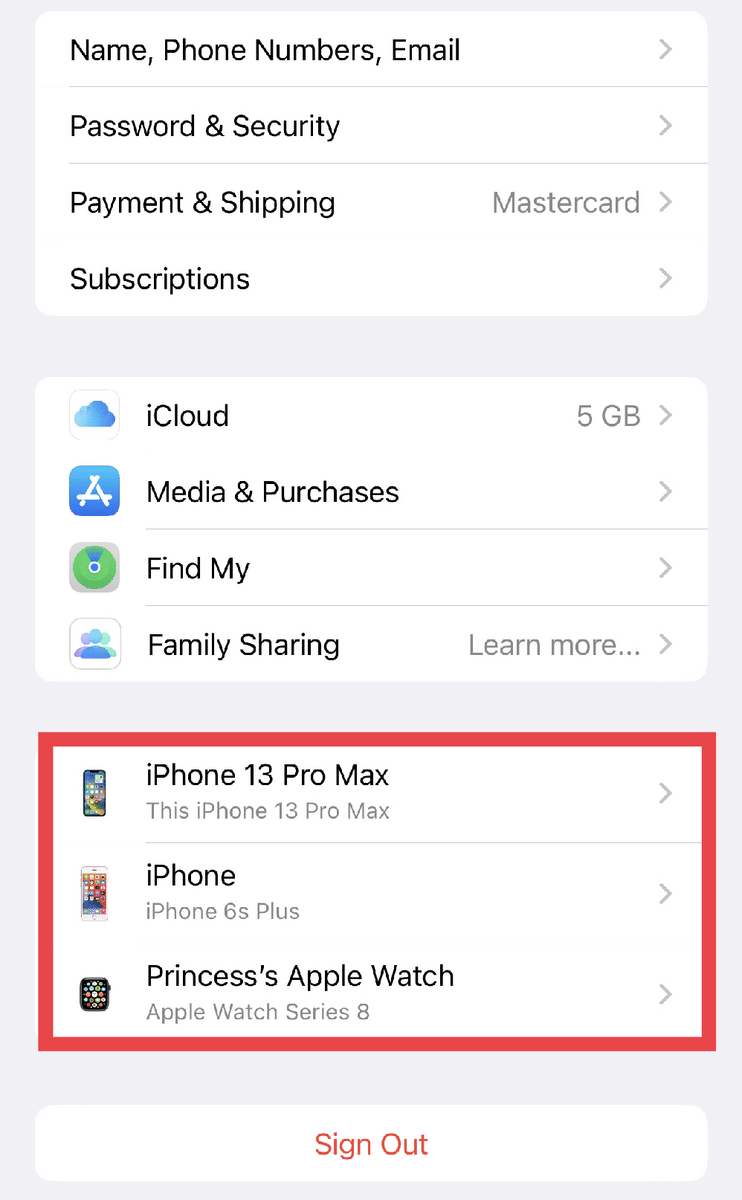
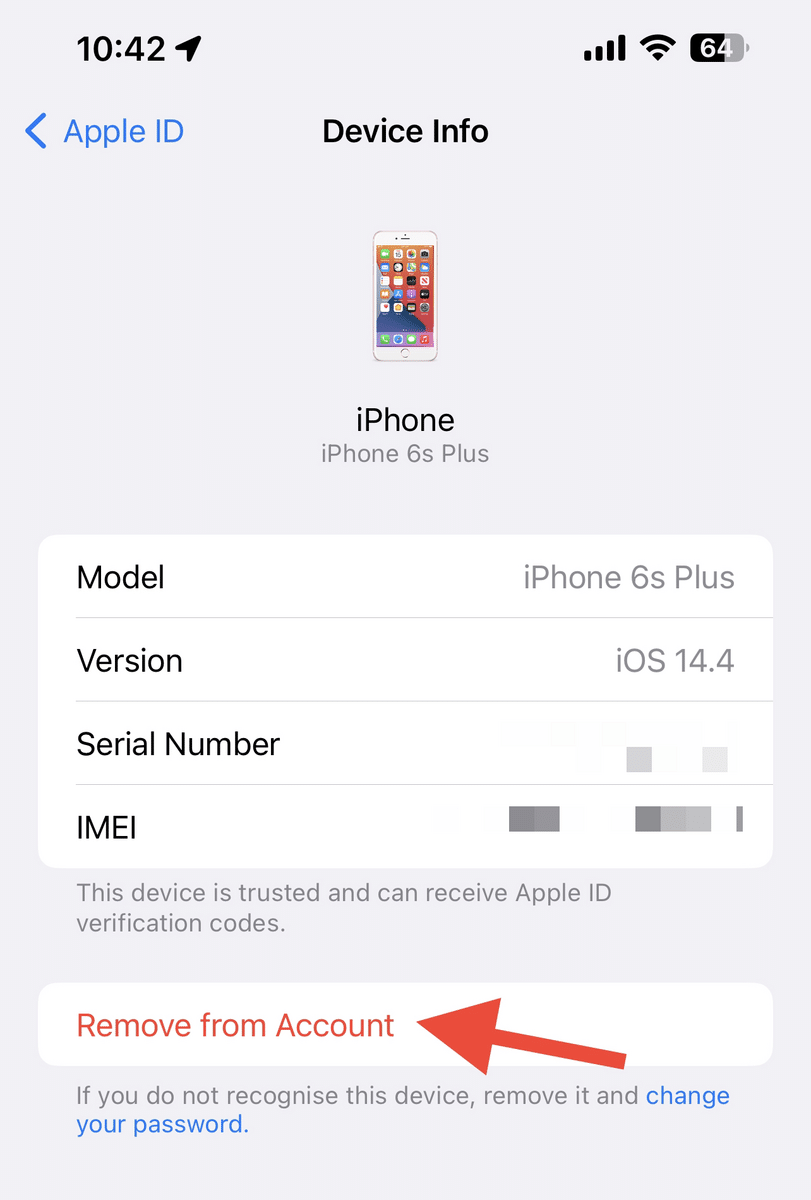
Below are the steps on how to stop someone from accessing your iPhone remotely:
- Sign in to Apple ID.
- Go to “Devices.”
- Select and review the device(s) that you want to remove.
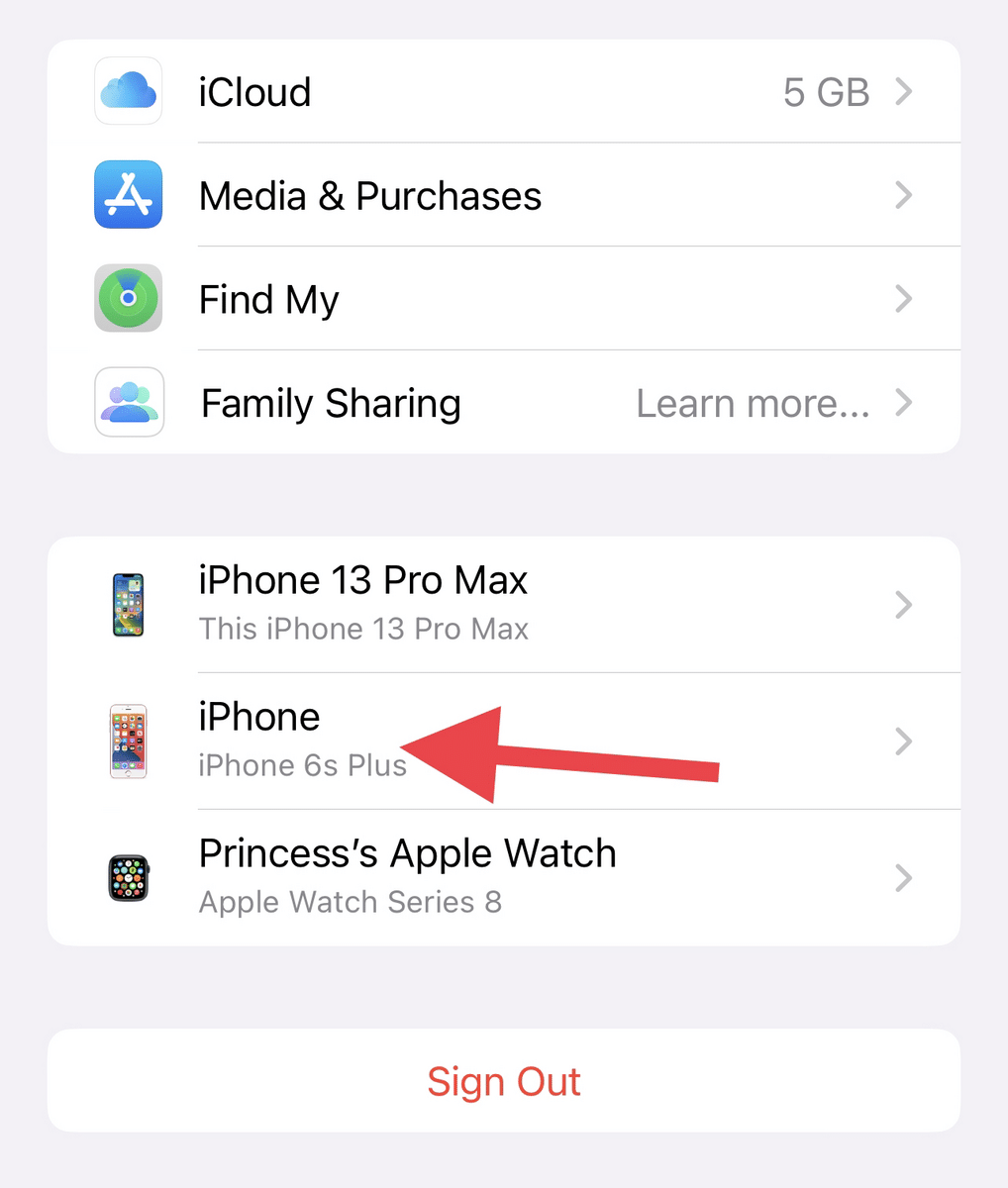
- If you wish to continue, choose “Remove from account.”
2. Check Your Apple ID
You can also see an overview of your security information through your Apple ID account, including the security actions you want to change. That’s why it’s good practice to check and configure your security measures regularly. This reduces the chance for attackers to control your phone remotely.
- Open the “Settings” app on your iPhone.
- Sign into your Apple ID account.
- Choose “Review your ID details.”
- Scrutinize your security details, such as your username, password, and email address.
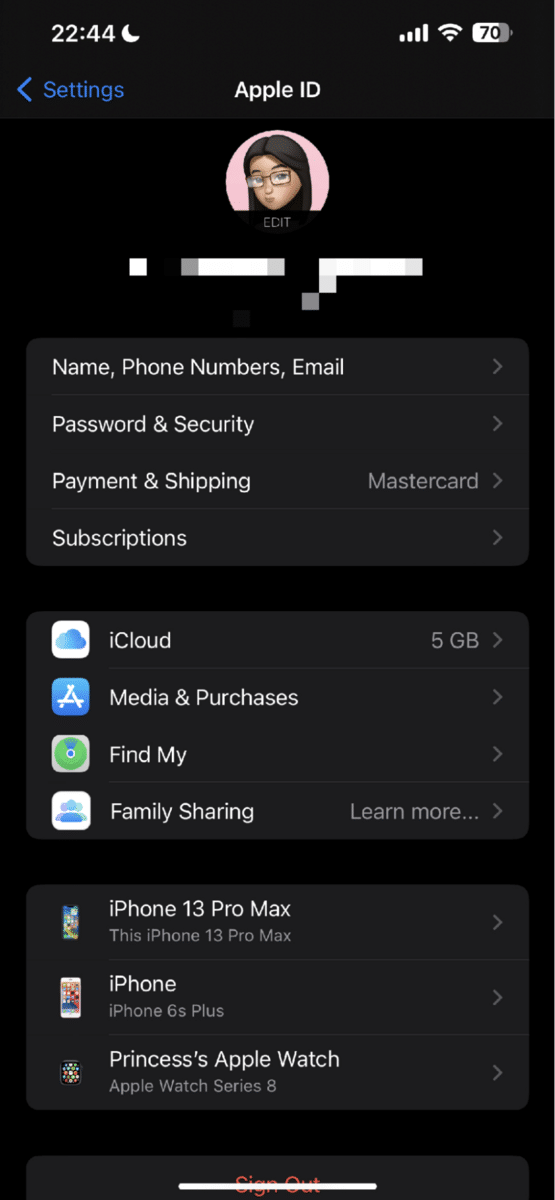
- For any present issue listed, follow the steps provided on your screen to fix it.
You should be good to go if you stop receiving Apple prompts. But if you really want to ensure your security features, consider changing your password. Here’s how:
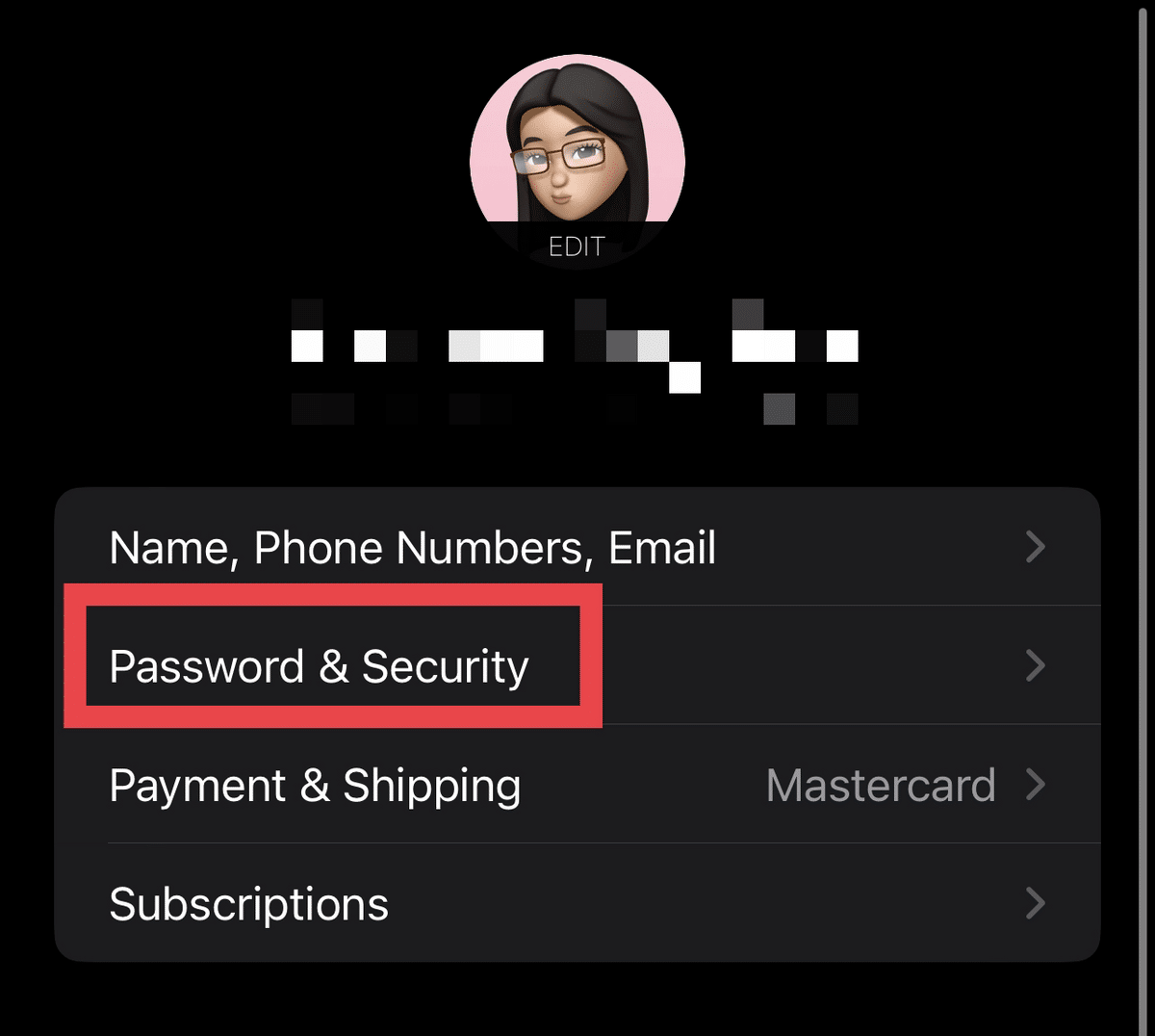
- Go to “Settings.”
- Tap your name, then select “Password & Security.”
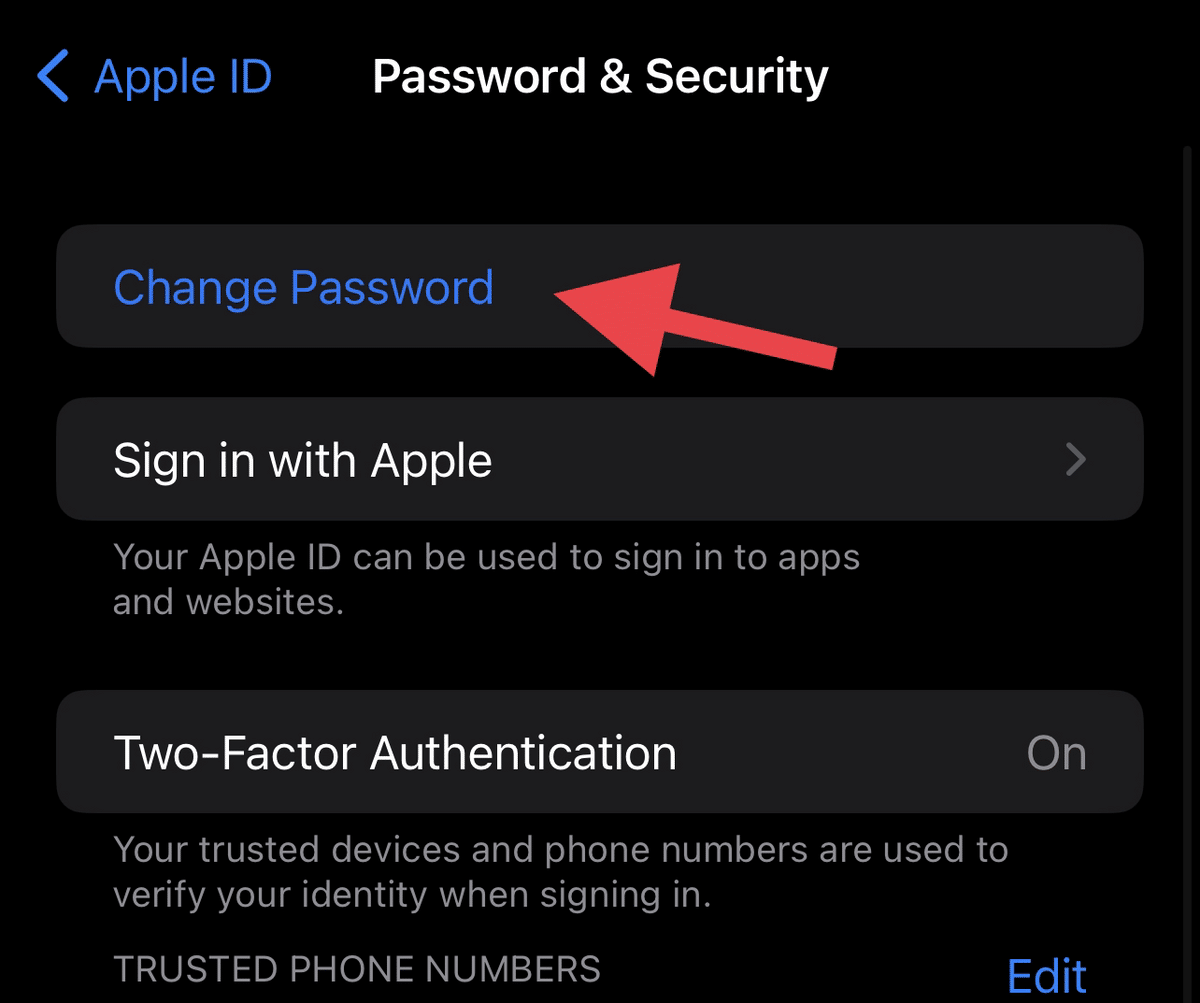
- Tap “Change Password.”
- Enter your iPhone passcode.
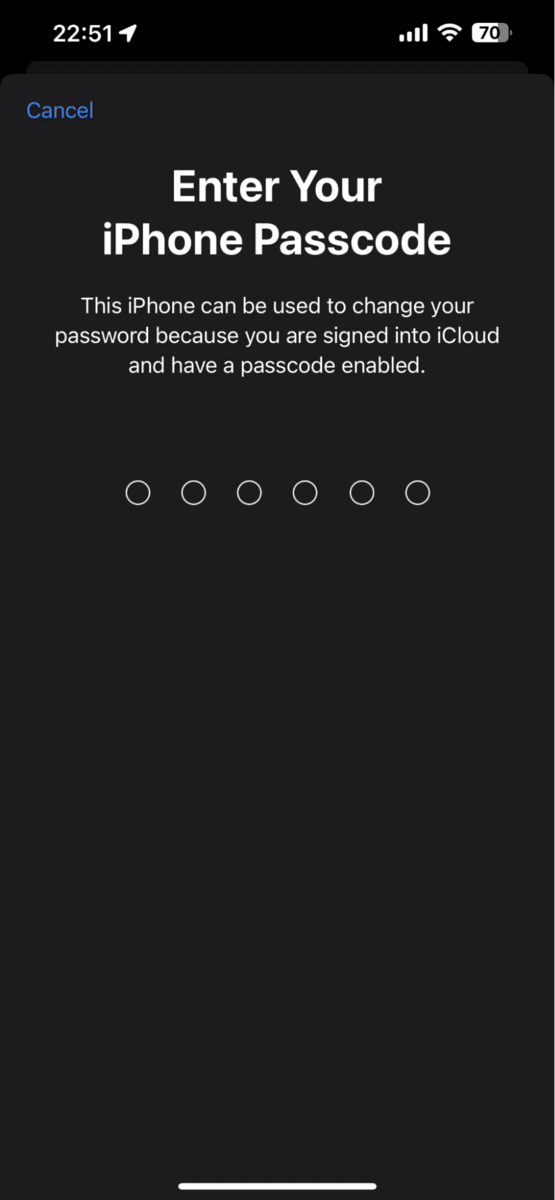
- Enter your new password and confirm it.
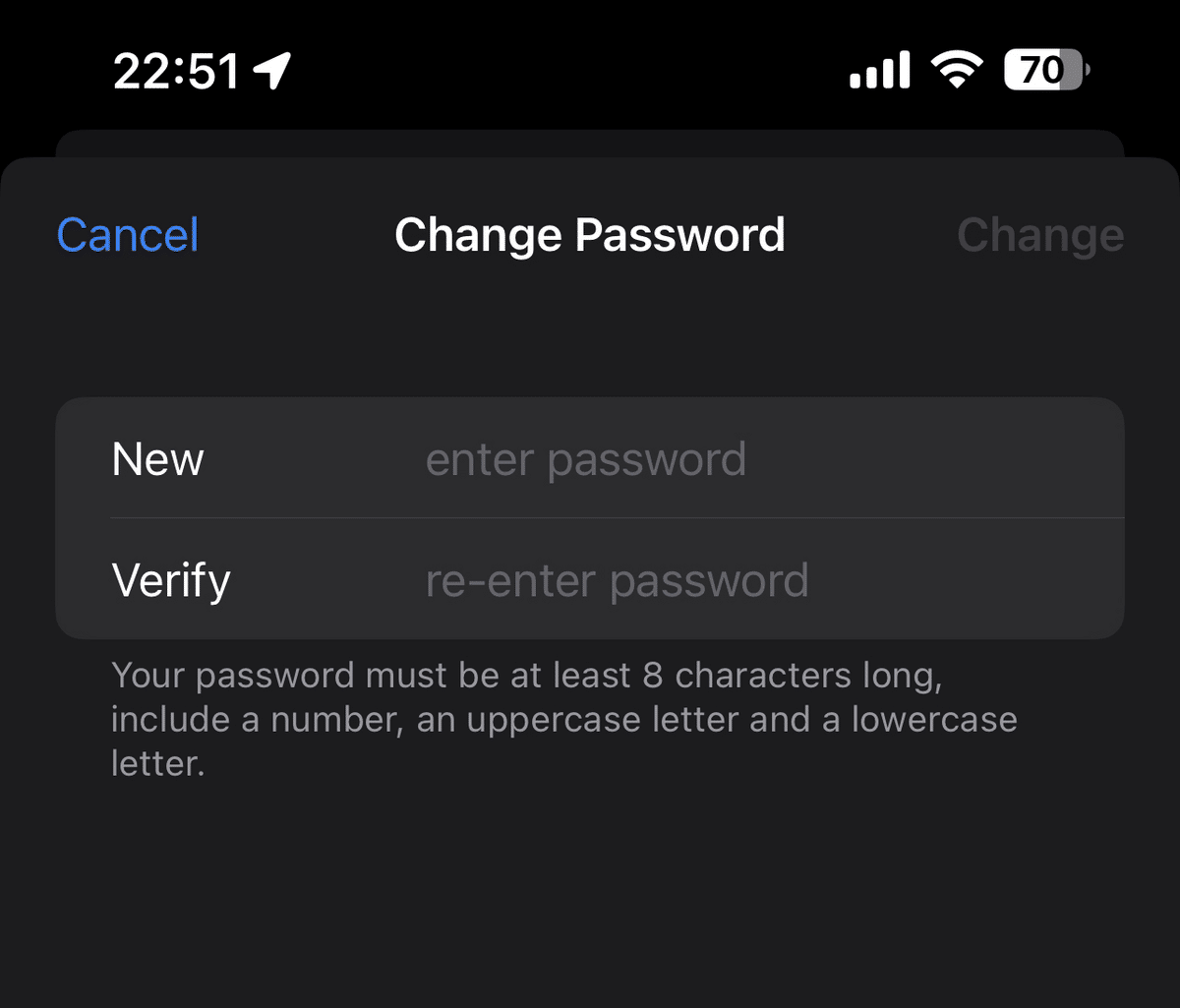
- Tap “Change” (it may appear as “Change Password” depending on the model).
3. Look for Other Face and Touch IDs
Signs of remote access can also manifest in your saved Face or Touch IDs. Check if there’s an unexpected one that you don’t remember adding. If you find one, it might indicate that other iPhone users are remotely accessing your iPhone.
The best way to prevent unauthorized iPhone users from accessing your phone is to delete the unrecognized ID and reset the security features. Here’s how to change your Face ID settings:
- Open “Settings” > “Face ID & Passcode.”
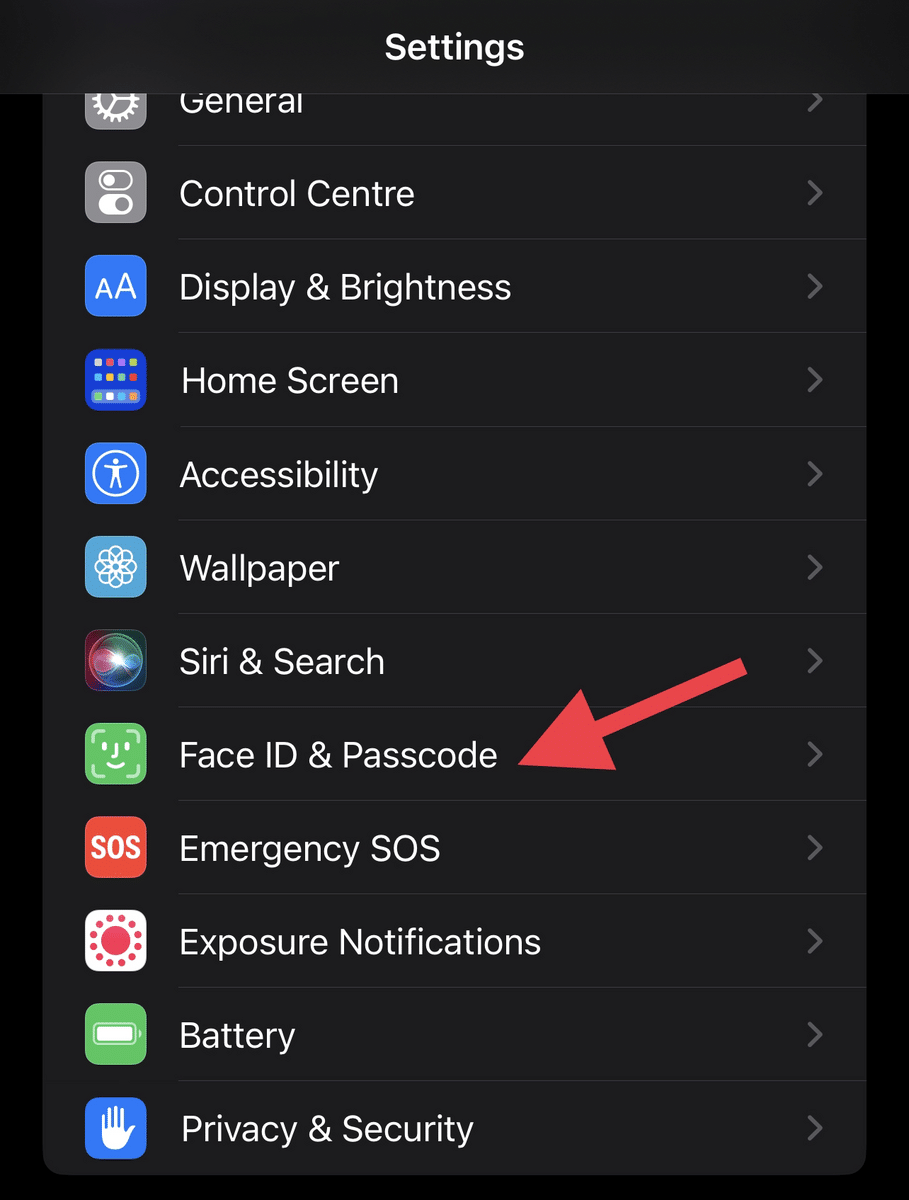
- Enter your passcode to continue.
- Tap “Reset Face ID.”
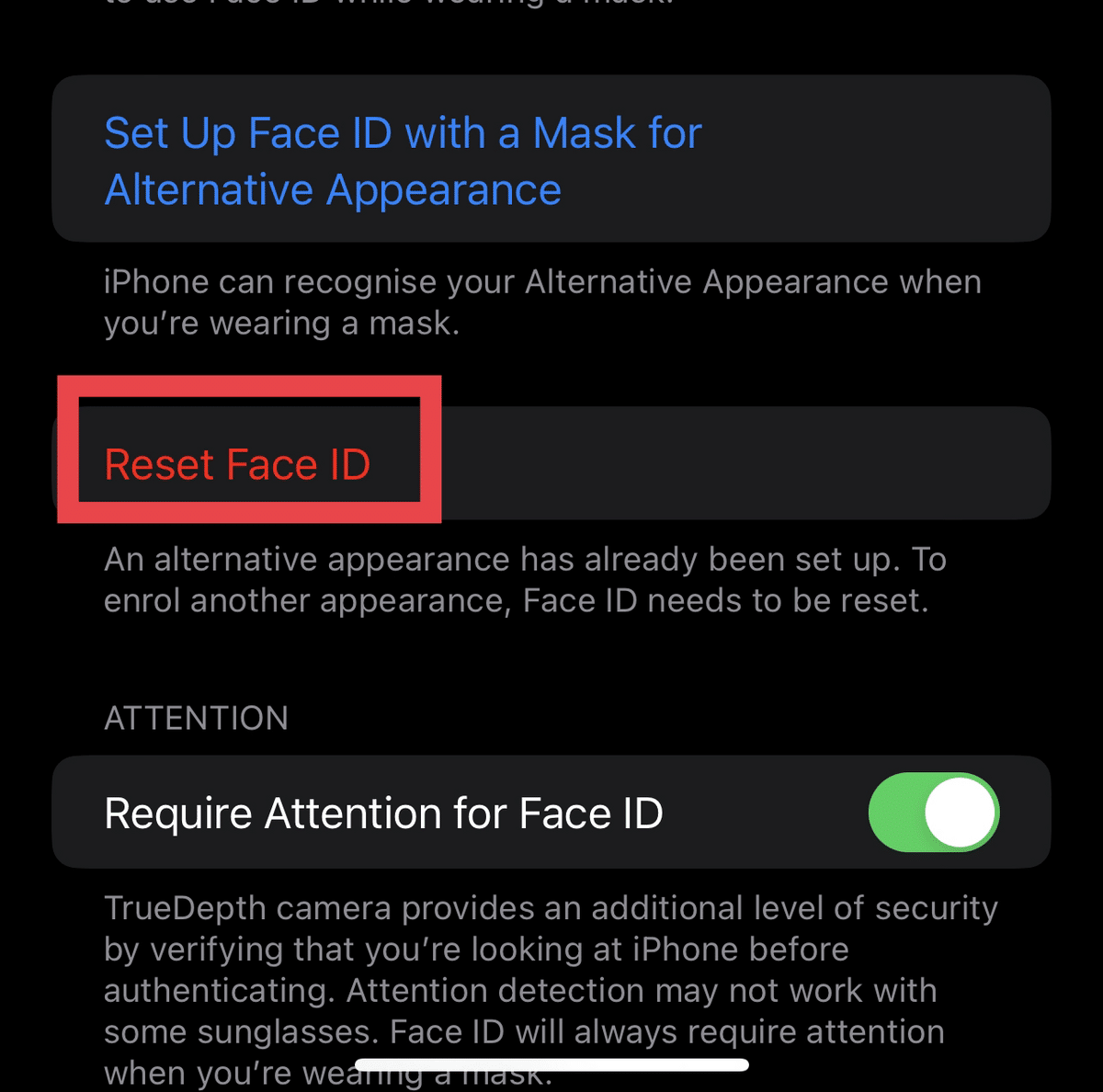
- Once it resets, tap “Set Up Face ID.”
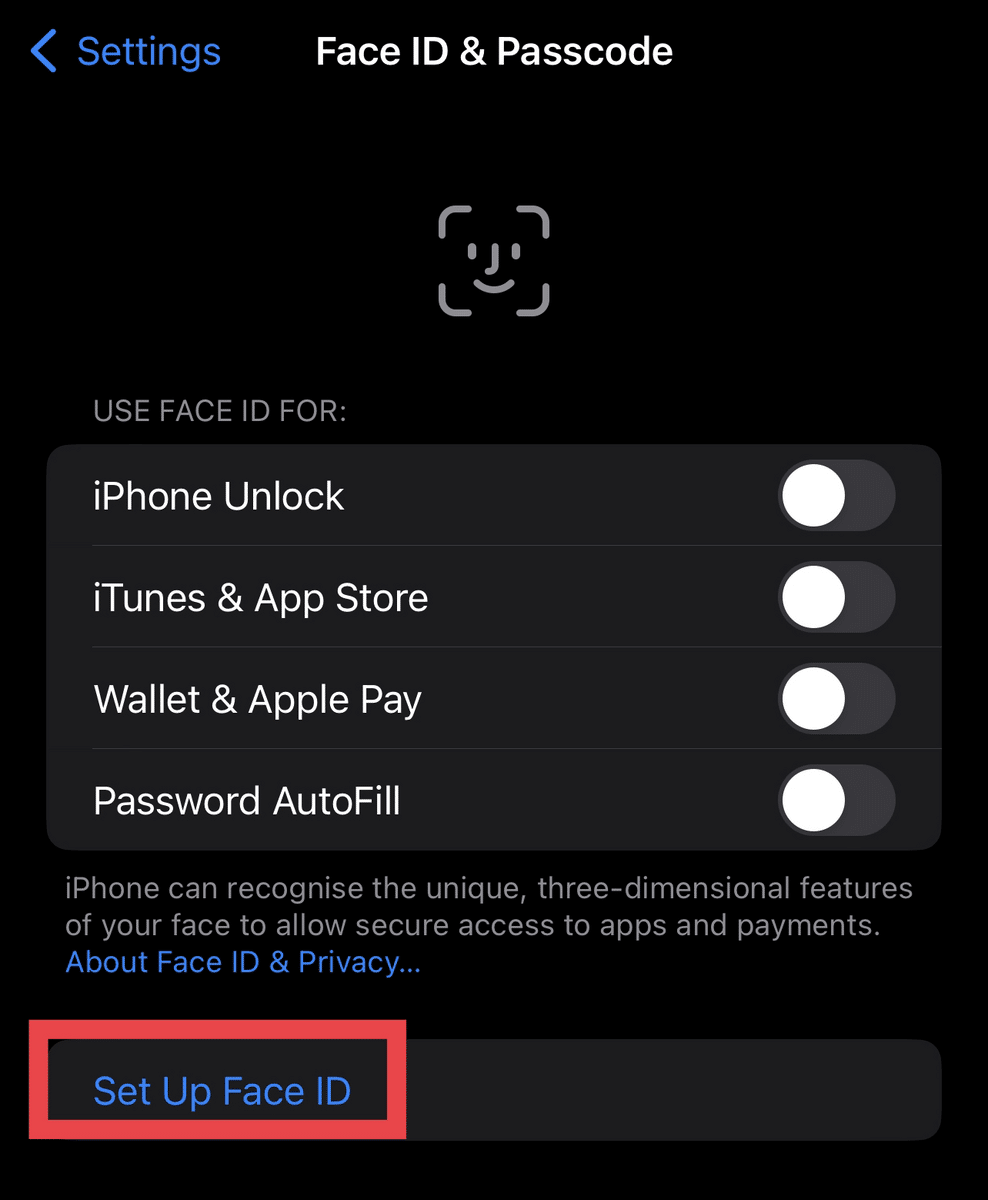
- Position your face within the provided frame on your screen.
- Let your iPhone scan your face by moving your head slowly in a circular direction.

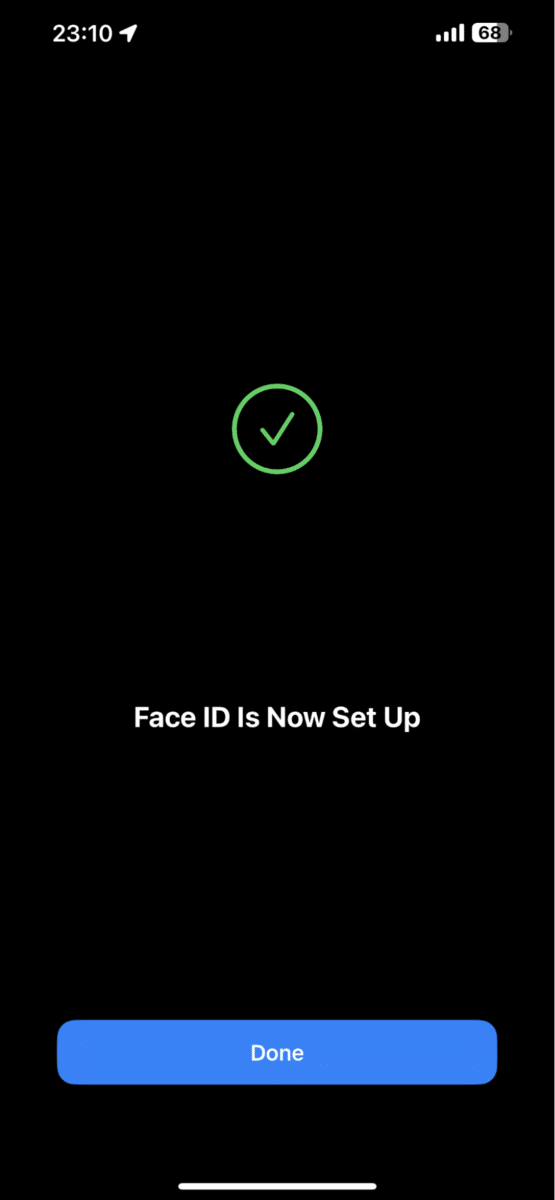
- Once the Face ID is set up, tap “Done.”
If you want to change your Touch ID options, you can follow the steps below:
- Go to “Settings.”
- Tap “Touch ID & Passcode.”
- Type in your passcode.
- Tap the fingerprint name that you want to remove.
- Tap “Delete Fingerprint.”
- If you want to set up another fingerprint, tap “Add a Fingerprint.”
- Place your finger on the Touch ID sensor to start the scan.
- Wait until your iPhone gives a haptic vibration, then lift your finger.
4. See Two-Factor Authentication Requests
One of the best security measures for your iPhone and your accounts is to enable two-factor authentication (2FA). This requires you to confirm (using an authorized mobile device) any significant modification happening on one of your accounts.
In this case, any bizarre 2FA requests appearing on your iPhone notifications indicate that someone’s trying to access your account or device from another unrecognized device.
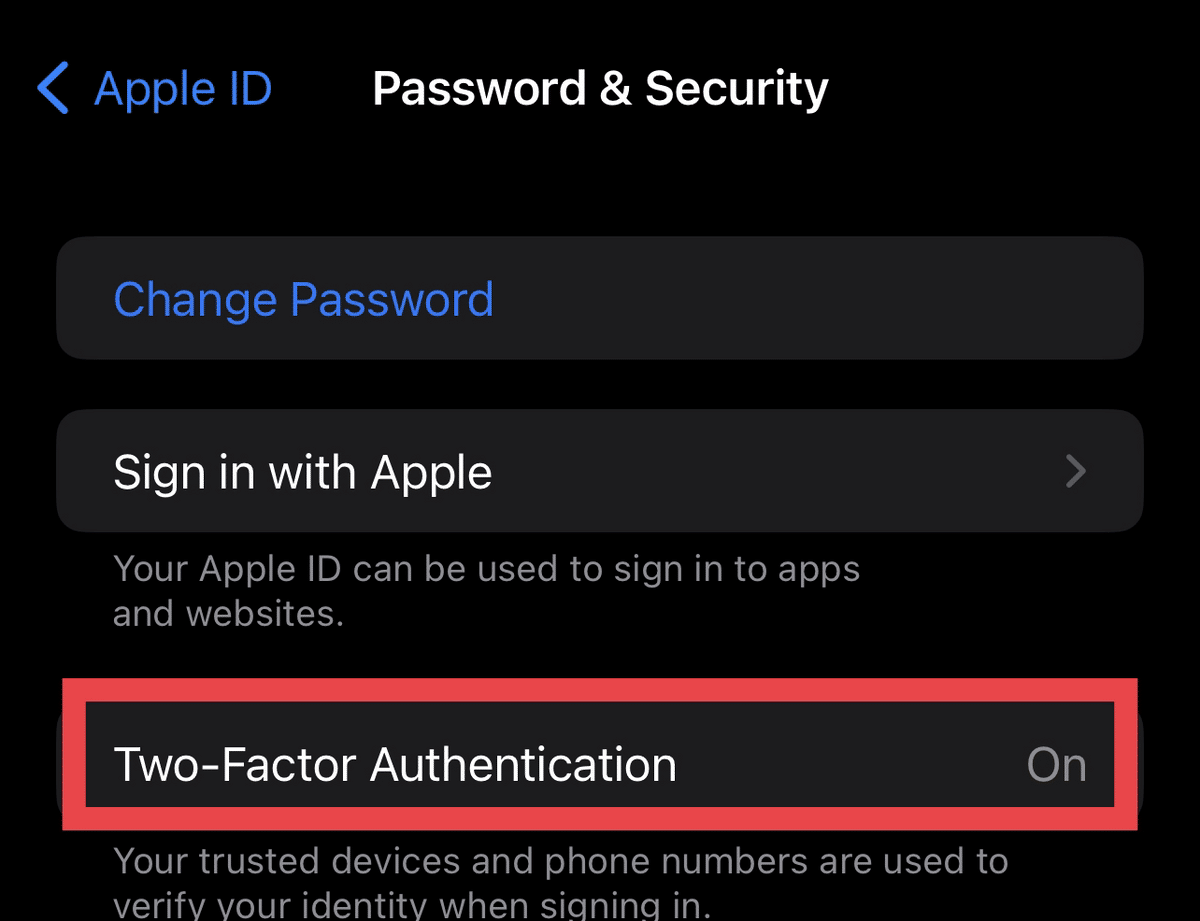
If you haven’t enabled two-factor authentication yet, here’s how you can set it up:
- Go to “Settings.”
- Tap your name > “Password & Security.”
- Tap “Turn On Two-Factor Authentication.”
- Tap “Continue.”
- Simply follow the steps displayed on your iPhone to finish the process.
5. Check If an App Is Remotely Accessing Your iPhone
Some unfamiliar apps that you accidentally install or get installed on your phone out of nowhere might give way to remote access. To check for such apps, try doing the following ios operating system security steps on your iPhone:
- Launch the Settings app on your iOS device.
- Tap “Privacy & Security.”
- Locate and tap “App Privacy Report.”
- Toggle on “Turn on App Privacy Report” to ensure your iPhone avoids unwanted access from apps.
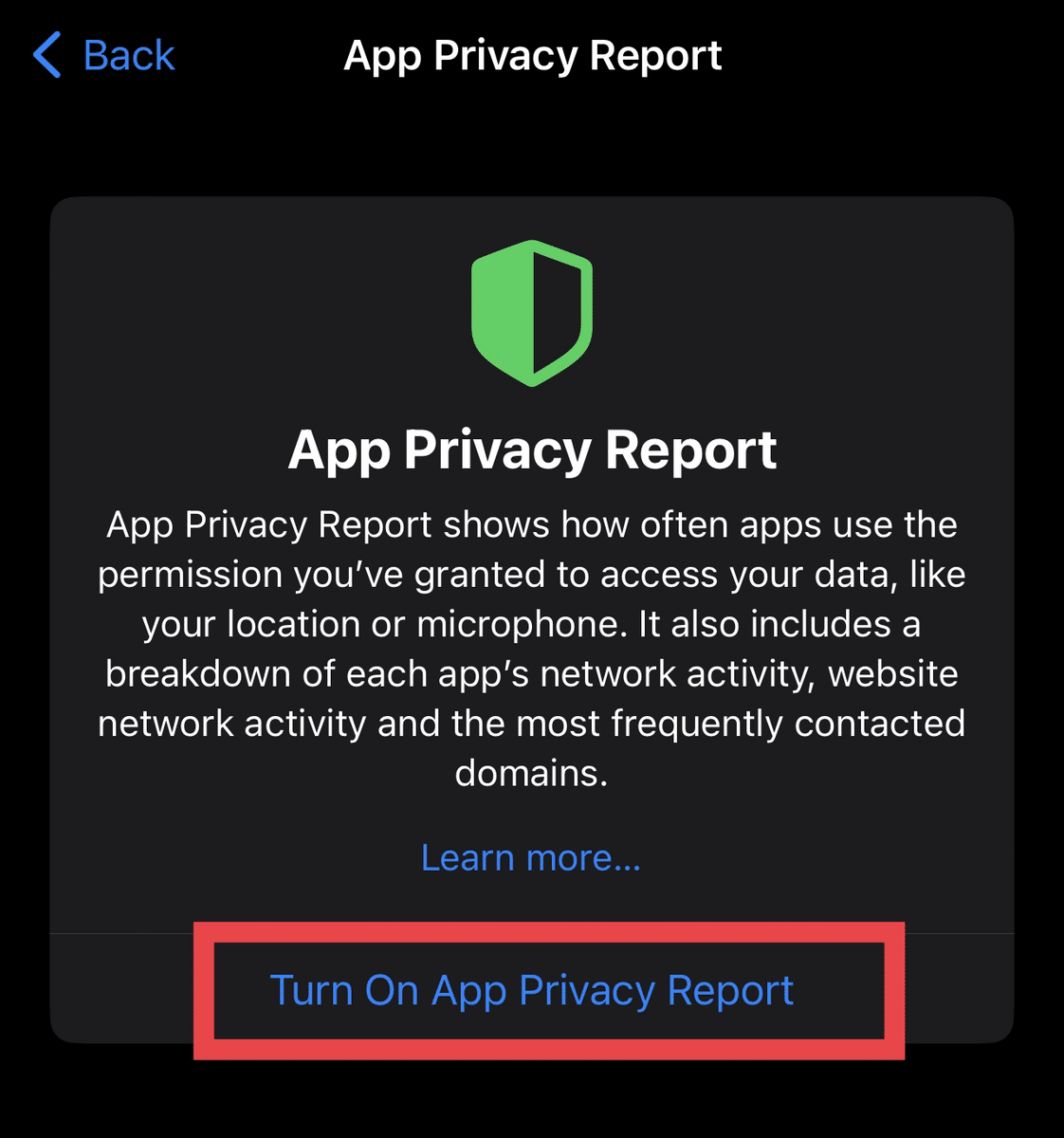
Once the report is generated, you can check how your installed apps interact with your private information. Scrutinize the apps that can access the sensitive data from your iCloud account extensively and see if they need to be remotely accessed.
The App Privacy Report can cover the apps’ behavior for up to one week.
Tips for Preventing Hackers from Accessing Your iPhone
Fixing the vulnerable points of your iPhone’s security is one thing. Preventing cyber attacks from happening is another. Here are a few other tips that you can apply to avoid security issues in the future:
1. Don’t Leave Your iPhone Unattended
Make it a habit to turn off your phone’s screen before leaving it. This way, anyone wanting to access your online account or iPhone while it’s unlocked and unattended would have no chance to do something bad to it (like install spyware).
As much as possible, you must not let anyone use your iPhone without your presence. For heightened security purposes, be sure to keep your iPhone somewhere that cannot be accessed by other people. If this isn’t possible, make sure to keep an eye on whomever you’re lending the device to.
2. Always Use a VPN When Using Public Networks
Public networks are a literal “hotspot” for security threats. By connecting to one without any layer of security, you’re risking your phone against adware, malware, spyware, and hackers.
A good security measure is using a virtual private network (VPN). This ensures that your Apple device connection to the internet is encrypted and secure.
If you’re not using your WiFi or Bluetooth, you should turn them off when going to public places. This way, anyone with malicious intentions won’t be able to connect to your phone remotely.
3. Configure App Permissions
When you want to install apps for the first time, it will usually ask you some security questions and ask you to grant access permissions to the various features of your device. As a rule of thumb, you want to grant access only to apps you can really trust. To further ensure your security, make sure that these apps are downloaded from the App Store. If you are uncertain about a particular app, you can contact Apple support for further advice.
For apps that don’t utilize certain permissions often, e.g., mic and camera access, it’s best to disable their remote access tool.
4. Keep Your Device Up-to-Date
iOS and software updates aren’t all about exciting new features. They’re also meant to patch up any loopholes in the current version’s security. Make sure to install these updates if they become available for your mobile devices.
Another way to make an update is to uninstall suspicious apps or files you’re not using. They not only have higher data usage on Apple devices but also serve as vulnerable points for malicious attackers.
5. Regularly Change Your Passwords
Changing your Apple ID passwords regularly lowers the chances of someone determining your current password, which could have allowed them to access your accounts without authorization remotely. Make sure to use secure passwords — an alphanumeric mix with capitalized characters and special symbols.
6. Use a Secure Browser
Malware usually attacks your device remotely when browsing the web. They can either be present via phishing (tricking a user into entering their information) or through suspicious links you visit.
While more advanced web browsers aren’t foolproof, they provide an extra layer of security. Examples of effective third-party software include Brave and Firefox. Some browsers can also prompt you about potential security threats from links you’ve clicked.
Final Thoughts
You might notice more signs that malicious people are accessing your Apple iPhone. If any of the indicators above manifest on your mobile device, raise a red flag with Apple Support. You can also investigate and check your online accounts for security breaches using this guide on how to tell if someone is accessing your iPhone remotely.
If you want to improve your cyber security knowledge, then check out this online course on Udemy that covers everything from security governance to network security, cyber attacks, malware, and more!
Related: